 MENU
MENU
 MENU
MENU
 Switch’s cyber management system is certified to ISO 27001 standards and 100% of the ISO 27001 requirements are covered/certified for our colocation services. A list of additional audit reports can be accessed on the audit reports page of our corporate website, by clicking here. Please email auditreports@switch.com for an approval code to access these reports.
Switch’s cyber management system is certified to ISO 27001 standards and 100% of the ISO 27001 requirements are covered/certified for our colocation services. A list of additional audit reports can be accessed on the audit reports page of our corporate website, by clicking here. Please email auditreports@switch.com for an approval code to access these reports.
Please reference our Acceptable Use Policy and our statement on GDPR Compliance for additional information regarding Switch’s programs and policies relating to the usage, collection, and protection of client data.
Switch has a structure in place for the oversight, compliance, and responsibilities for cybersecurity.
Please reference directly below for additional information.
INFOSEC responsibilities and methods:
Administering risk assessments based on the NIST Cyber Security Framework (CSF), NIST 800-30, and ISO 27001:2013 ISMS.
METHODS: Real Time Analysis of Threats, Adherence to Regulatory Standards, Assuring Preventive Controls are in place and functional.
What we do: Switch is a colocation data center provider. Colocation data centers provide a shared physical environment for enterprise clients to “co-locate” their mission critical IT infrastructure. Our business operations entail the provision of space, power, cooling, and physical security for the servers, storage arrays, and networking equipment owned and operated by our clients. In addition to colocation services, Switch also provides access to a variety of telecommunications and network service providers at a minimum cost and complexity.
What we do not do: Switch does not manage, maintain, control, or have visibility to the data residing on its clients’ servers or data transmitted to/from the telecommunications networks connected to our data centers. Moreover, Switch does not directly engage in the provision of cloud services, managed hosting, software, or logical security services that may involve the collection of, or responsibility for client data. As such, our contracts stipulate that clients shall maintain full right of access, rectification, and deletion of their data at all times.
Switch has several programs and policies in place related to data security and the protection and privacy of client data.
Security Breach Disclosure: Switch has not experienced a breach in security since its founding in 2000.
Switch has operational measures in place to monitor and respond to data breaches and cyberattacks. Please reference directly below for additional information.
Annual Cyber Risk Assessment
A cyber risk assessment is conducted annually by our Information Security team. This involves the identification of, and mitigation plan for key risks, including:
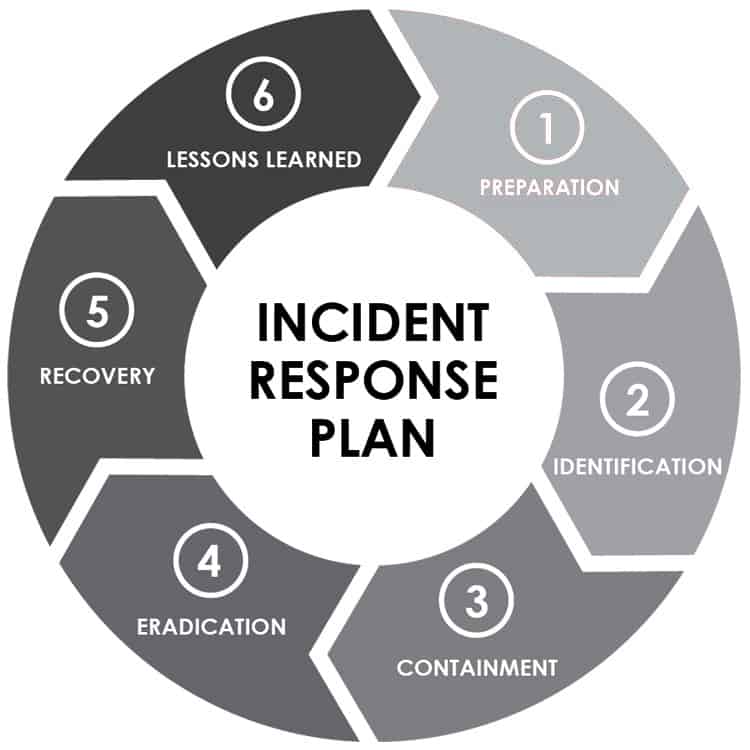
Incident Response Plan (IRP)
An Incident Response Plan (IRP) has been developed as an integral component of Switch’s overall information security program. The IRP includes action plans that deal with intrusions, data theft, denial of service (DoS), and other IT security-related incidents. The six major steps of the IRP are designed to ensure Switch is prepared to effectively detect and respond to incidents in an effective manner to minimize adverse impacts and provide lessons learned.
The IRP steps are as follows:
Cyber Kill Chain
Switch InfoSec uses the Cyber Kill chain model for intelligence used to identify and prevent intrusion activity. The model identifies what the adversaries must complete in order to achieve their objective.
Switch SAFE
Switch SAFE is a scalable DDOS mitigation service available for client use at every Switch data center campus location. It is a sophisticated system of software applications and hardware appliances that support client data security. Click here for additional information regarding Switch SAFE.
Switch has a policy in place for regular internal security audits that address vulnerability assessments or penetration testing of the company’s systems, products and practices affecting user data. Please reference directly below for additional information.
Vulnerability Management
Automated scans are continuously conducted on the entire Switch Information System, this includes the critical infrastructure that is segmented and access controlled. Information Security is responsible for ensuring that the signatures used by the Vulnerability Assessment Suite are updated periodically.
Penetration Testing
A third-party penetration test is conducted semiannually. The scope of these regular tests are as follows:
Switch has a policy in place for its employees to undergo regular training on Information Security Awareness. Please reference directly below for additional information.
Information Security Awareness
All Switch employees are required to complete the Information Security Awareness Training module on an annual basis, which includes an exhaustive review of our internal policies relating to Cybersecurity and Data Privacy. This information is also provided in the Employee Handbook, and must be attested to and signed by each employee on an annual basis.
Cybersecurity Program Plan (CSPP)
The Switch Cyber Security Program reflects our commitment to implement leading data protection
standards on behalf of our clients and with respect to our own internal data systems. Its primary mission is to protect the Confidentiality, Integrity, and Availability of the Switch Information System. Thus, the CSPP outlines a framework for implementing a defense-in-depth layered protection approach that consists of complementary technical, operational, and management controls for the Switch Information System.
Program Scope
The CSPP applies to the entire Switch Information System (any system that stores, process, or transfers Switch data), which includes support systems, major applications, and minor applications. In accordance with the IT Information Security Policy, NIST 800-53 Risk Assessment, and ISO 27001 ISMS, the CSPP describes the requirements designed to sustain a defense-in-depth approach for protecting the Confidentiality, Integrity and Availability of the Switch Information System. It provides guidance and requirements for the implementation of security controls to protect Switch from cyber-attacks and threats, thus minimizing any impacts to the systems and information that are necessary to manage and operate Switch facilities and services.
Physical and Environmental Security
As a trusted service provider of the world’s only Class 5 Platinum data center facilities, we are fully focused on delivering physical and environmental security for our data centers worthy of supporting mission-critical deployments. Third-party audited reports regarding our compliance with these initiatives are available upon request. Simply email auditreports@switch.com for assistance. You may also visit https://www.switch.com/audit-reports/
Incident Response and Reporting Mechanisms
Switch is committed to notifying data subjects (including client representatives and Switch employees) in a timely manner with respect to policy changes and/or any known incidents regarding the breach of client data.
The Switch Network Operations Center (NOC) is available 24/7/365 for data subjects to raise concerns about data privacy. Users are the first line of defense, as they are likely to detect any odd behaviors within their systems. The Switch NOC provides an incident response support resource to offer advice and assistance to users of the information system for the handling and reporting of security incidents. Users are required to notify the NOC of an obvious or potential cyber security-related event occurring on any Switch system.
Additionally, the Switch Ethics Hotline is a third-party, anonymous reporting hotline allowing users to report incidents related to ethical and compliance concerns/violations.
Privacy Risk Assessments and Third-Party Audits
Various independent audits are conducted annually by Schellman & Company regarding Switch’s technologies, security protocols, and practices affecting the privacy of user data.
ISO CERTIFICATE DIRECTORY
Other audit reports include: SOC 1, SOC 2, SOC 3, MPAA, PCI DSS-ROC, PCI DSS-AOC, NIST 800-53 (Type 1), HIPAA (Type 1). These reports are available upon request at https://www.switch.com/audit-reports/
Switch maintains a library of additional policies and procedures to ensure its services are Tier 5 Platinum compliant and meet Switch’s aggressive sustainability standards. Switch secures these policies on site, to avoid the security risks of espionage, terrorism, sabotage, and cyber attack, inherent in unauthorized duplication, proliferation, or exploitation of these policies. If you would like additional detail or an on-site tour of Switch’s facilities to inspect these policies, please contact the Investor Relations Team (investorrelations@switch.com) or the Switch Policy team (policy@switch.com).